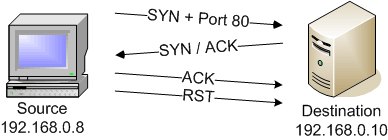
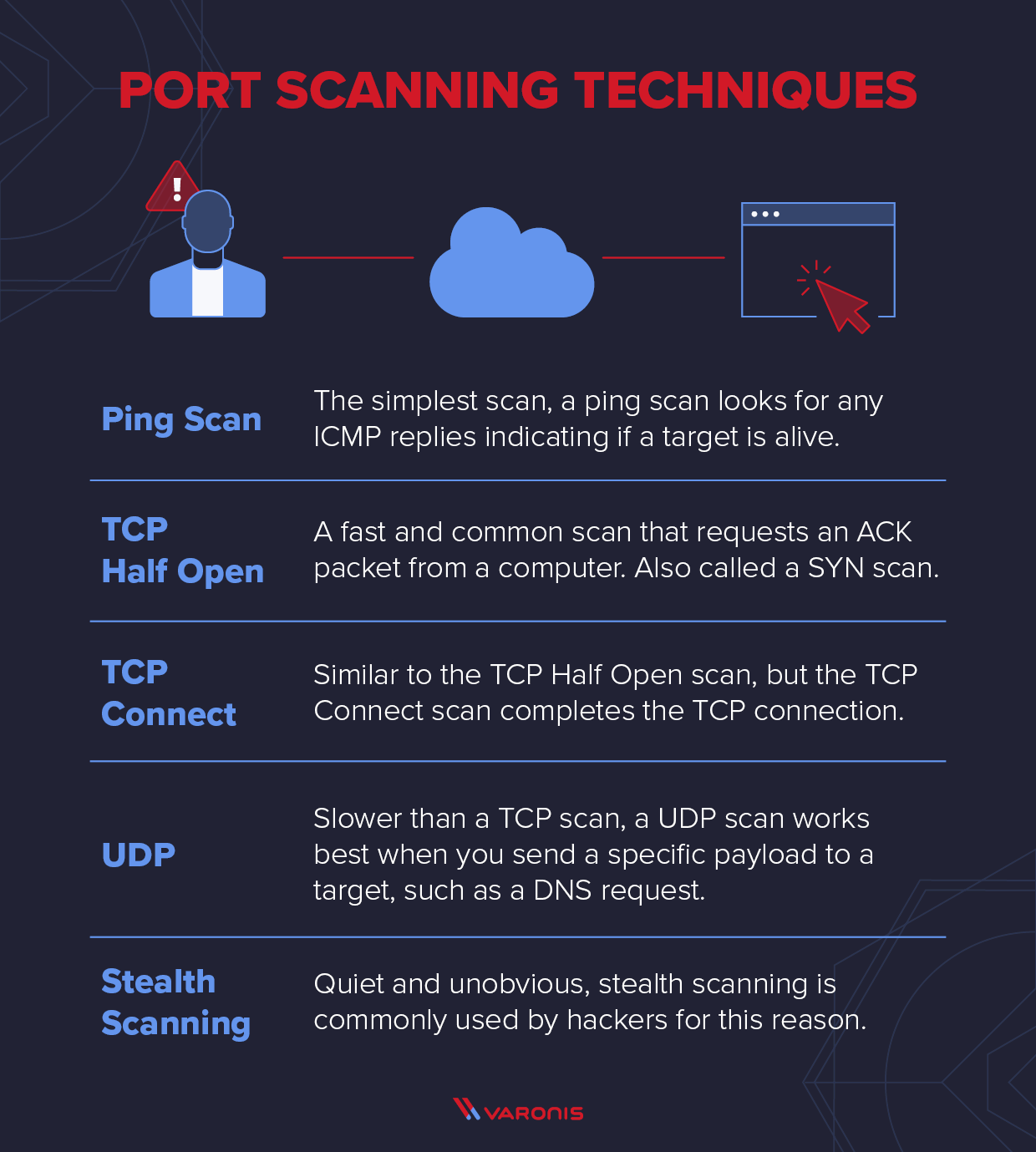
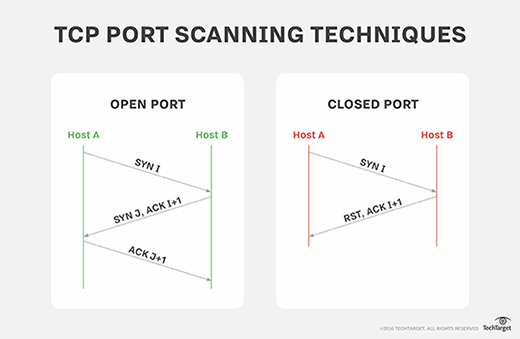
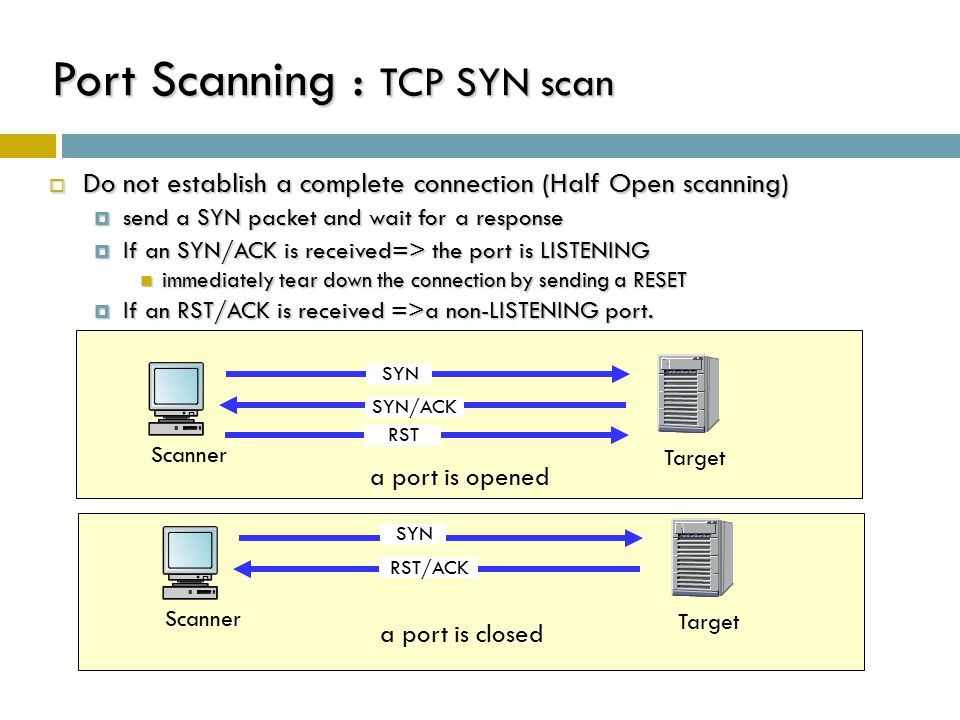
Port Scanning > Penetration Testing and Network Defense: Performing Host Reconnaissance | Cisco Press

TCP SYN scan: static versus dynamic results of what the sensors saw in... | Download Scientific Diagram

NMAP – How to run an NMAP -sS SYN Stealth Scan on Windows 7 – The Visual Guide | University of South Wales: Cyber University of the year: Three years running: 2019, 2020, 2021