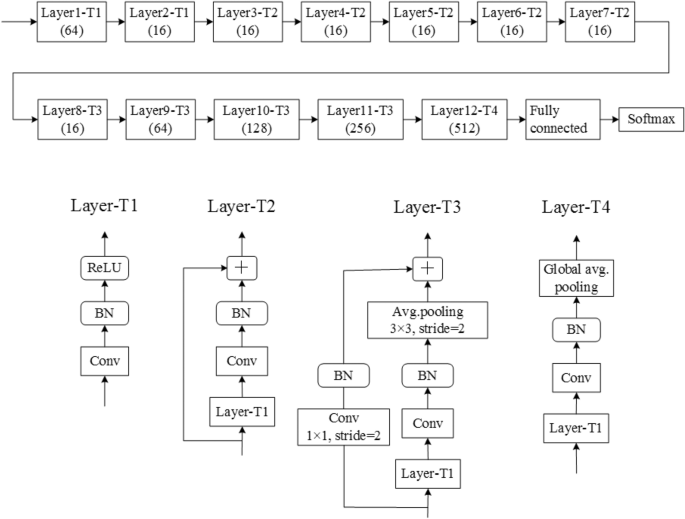
![PDF] CIS-Net: A Novel CNN Model for Spatial Image Steganalysis via Cover Image Suppression | Semantic Scholar PDF] CIS-Net: A Novel CNN Model for Spatial Image Steganalysis via Cover Image Suppression | Semantic Scholar](https://d3i71xaburhd42.cloudfront.net/7114514f2782ff65dad0ff435835b15575783556/7-Figure7-1.png)
PDF] CIS-Net: A Novel CNN Model for Spatial Image Steganalysis via Cover Image Suppression | Semantic Scholar

Steganography - A review Lidan Miao 11/03/03. Outline History Motivation Application System model Steganographic methods Steganalysis Evaluation and benchmarking. - ppt download

Towards blind detection of low‐rate spatial embedding in image steganalysis - Farhat - 2015 - IET Image Processing - Wiley Online Library
Steganalysis of JSteg algorithm using hypothesis testing theory – topic of research paper in Mathematics. Download scholarly article PDF and read for free on CyberLeninka open science hub.

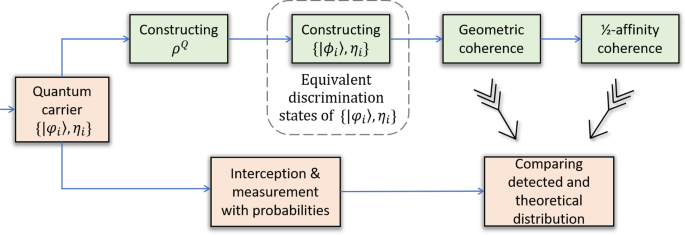
A novel coherence-based quantum steganalysis protocol | Qu, Zhiguo; Huang, Yiming; Zheng, Min | download

1 A Markov Process Based Approach to Effective Attacking JPEG Steganography By Y. Q. Shi, Chunhua Chen, Wen Chen NJIT Presented by Ashish Ratnakar and. - ppt download

Towards blind detection of low‐rate spatial embedding in image steganalysis - Farhat - 2015 - IET Image Processing - Wiley Online Library